
![Screen shot of message from 'Command Processor' of Windows Vista for blocked program [Screen shot of message from 'Command Processor' of Windows Vista for blocked program]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure16(en-us,technet.10).jpg)
- Purpose
- Reason
- Impact
- Operation
- Advanced Logging
- Availability and Vulnerability
- Reliability and Safety
- Interoperability and Security
- Prerequisites
- Loopholes, Limitations, Dependencies and Bugs
- Details
- Background Information
- Fallacies, Misconceptions and Myths
- Implementation and Build Details
- Authenticity and Integrity
- Download
- Installation
- Automatic online installation
- Manual offline installation
- Test
- Update
- Upgrade
- Deinstallation
- Bugs
![Screen shot of message box from 'Windows Explorer' of Windows Vista for blocked program [Screen shot of message box from 'Windows Explorer' of Windows Vista for blocked program]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure15(en-us,technet.10).jpg)
Purpose
The
setup scripts
NTX_SAFER.INF
(for Windows 8 and newer versions of
Windows NT),
NT6_SAFER.INF
(for Windows Vista®,
Windows Server 2008, Windows 7 and
Windows Server 2008 R2) and
XP_SAFER.INF
(for Windows XP, Windows Server 2003 and
Windows Server 2003 R2) configure
Software Restriction Policies
alias
SAFER
with a proven and well-tested ruleset on all
(including Embedded, Home and
Starter) editions of Windows XP,
Windows Server 2003,
Windows Server 2003 R2, Windows Vista,
Windows Server 2008, Windows 7,
Windows Server 2008 R2, Windows 8,
Windows Server 2012, Windows 8.1,
Windows Server 2012 R2, Windows 10,
Windows Server 2016, Windows Server 2019,
Windows 11 and Windows Server 2022.
Note: the
setup script
NTX_SAFER.INF
removes overwrites the bogus
AppLocker registry entry which disables
SAFER on Windows 11 22H2!
This technique is known as Application Whitelisting;
the setup scripts presented here perform a rather permissive
implementation: they allow execution of all applications which are
properly installed by an administrator.
Note: the
MSDN article
Security Considerations: Microsoft Windows Shell
provides details for proper installation!
Reason
Together with Windows’
Access Control,
the SAFER ruleset implements for the
NTFS
file system the equivalent of
DEP
alias
W^X
in the virtual memory: execution is denied in all
directories where unprivileged (standard) users are allowed to write
(i.e. create, modify or replace) files or create directories, and
allowed only in directories where they are denied to write files or
create directories.
More precise: for users without administrative privileges execution
is allowed only
• in the directory %SystemRoot%\ (typically
C:\Windows\) and its subdirectories,
• in the directory %ProgramFiles%\ (typically
C:\Program Files\) and its subdirectories,
on systems with AMD64 alias x64 processor
architecture also
• in the directory %ProgramFiles(x86)%\
(typically C:\Program Files (x86)\) and its
subdirectories;
execution is denied in all other directories and their
subdirectories.
Note: the SAFER ruleset takes care of
NTFS
Alternate Data Streams
too!
Unlike unreliable, unsafe and vulnerable antivirus
software which almost always fails to detect new or unknown
malware (ransomware,
trojan horses, viruses, worms, …), known as
false negative
, or misdetect legitimate clean software as
malware, known as
false positive
, this method effectively stops all kinds of
known as well as new or unknown
malware and all other
unwanted or unauthorised software that uses executable files to
infest Windows NT installations, while allowing all
legitimate software to run, without introducing new
vulnerabilities or weaknesses!
The TechNet
article
Security Content Overview
states in the section Client Hardening
:
Software restriction policies are a key security feature of Windows
XP that can be used to lower the risk of users installing or running
unauthorized software, including potentially dangerous viruses or
other types of malicious software. Microsoft also recommends that
organizations give their users the minimum privileges that they need
to perform their job functions. Users with administrative rights may
be able to bypass many of the security countermeasures you put in
place.
Impact
U(nprivileged u)sers who are subject to
Software Restriction Policies
- are still able to download arbitrary (executable) files from
arbitrary web sites, to receive arbitrary (executable) files as
attachments of mails, etc. and store them anywhere they are allowed
to write files, but they can’t execute these files any more;
- can execute all Win32 applications that meet the
minimum requirements of the more than 25 year old
Designed for Windows
specification, i.e. have their executable files installed beneath
the directories
%ProgramFiles%\ or
%SystemRoot%\;
- can’t execute applications installed in their
User Profiles, stored on external, portable or
removable devices and media, or on other computers;
- can open all files with any application installed on their machines
by their administrators, i.e. they can work with all their documents
and all local applications without any restriction.
Warning: some imbeciles who don’t recognise
the simple word data in the directory pathnames
%ProgramData%\ alias
%SystemDrive%\ProgramData\, typically
C:\ProgramData\, %APPDATA%\ alias
%USERPROFILE%\AppData\Roaming\ alias
%SystemDrive%\Users\‹username›\AppData\Roaming\,
typically
C:\Users\‹username›\AppData\Roaming\, or
%LOCALAPPDATA%\ alias
%USERPROFILE%\AppData\Local\ alias
%SystemDrive%\Users\‹username›\AppData\Local\,
typically
C:\Users\‹username›\AppData\Local\, and
are unable to realise its meaning, install or place but executable
files below these directories!
For a recent demonstration of such gross incompetence see the
MSKB
article
4052623.
For current and previous offenses see for example the
Teams Desktop App shipped and installed with
Windows 11, the OneDrive Client
shipped and installed with Windows 10,
Mozilla Firefox, Mozilla Thunderbird,
Google Chrome, Google Drive, ….
Caveat: the setup scripts
NT6_SAFER.INF and NTX_SAFER.INF deny
execution for unprivileged users underneath the directory
%SystemRoot%\System32\DriverStore\, where imbeciles
from
AMD®,
Intel® and
nVidia® unfortunately install
their (graphic) drivers lately, subverting the DriverStore
,
introduced with Windows Vista as repository for drivers
and used as staging area during their installation; one of its
intended purposes is to enable the easy repair of installed drivers
in case of corruption.
If you want to use such braindead setup drivers,
add a path rule to allow execution in their staging directory
%SystemRoot%\System32\DriverStore\FileRepository\‹filename›.inf_‹architecture›_‹MD5 hash›\.
Note: exemption of privileged users from
Software Restriction Policies
leaves no loophole!
Privileged users can write files in the directories where execution
is allowed, can disable or remove
Software Restriction Policies and can thus execute any
file.
If you want or need to restrict administrators too, use the setup
scripts
NT6_SUPER.INF
(for all editions of Windows Vista,
Windows Server 2008, Windows 7 and
Windows Server 2008 R2) or
XP_SUPER.INF
(for all editions of Windows XP,
Windows Server 2003 and
Windows Server 2003 R2).
Caveat: on Windows 7 and newer
versions of Windows NT, all SAFER security
levels except Unrestricted
alias Fully trusted
are
equivalent to Disallowed
and deny execution!
Determine Your Application Control Objectives:
SRP on
Windows Vista and earlier supported multiple security levels. On
Windows 7 that list was restricted to just two levels: Disallowed
and Unrestricted (Basic User translates to Disallowed).
Note: user accounts created during
Windows Setup are but privileged
user administrator accounts!
Change their
account type
to Standard User (on Windows Vista and
newer versions of Windows NT) or
Limited User (on Windows XP,
Windows Server 2003 and
Windows Server 2003 R2) respectively if you use them
for your routine work!
Change a user’s account type:
When you set up Windows, you were required to create a user account.
This account is an administrator account that allows you to set up
your computer and install any programs that you'd like to use. Once
you finish setting up your computer, we recommend that you create a
standard account and use it for your everyday computing. If you
create new user accounts, you should also make them standard
accounts. Using standard accounts will help keep your computer more
secure.
Note: the dumb
User Accounts
control panel applet denies to demote the last or only privileged
user account even if the builtin (real) Administrator
account is activated!
Use the real User Accounts control panel applet
instead: to start it, run one of the equivalent command lines
Control.exe UserPasswords2
NetPlWiz.exe
RunDLL32.exe NetPlWiz.dll,UsersRunDll
with administrative privileges and access rights.
If you prefer the command prompt over the graphical user interface,
run the following command lines with administrative privileges and
access rights:
Net.exe LOCALGROUP Administrators "%USERNAME%" /Delete
Net.exe LOCALGROUP Users "%USERNAME%" /Add
Caveat: don’t forget to
enable
the builtin Administrator account; run the command line
Net.exe USER Administrator /Active:Yes /PasswordReq:Yes
with administrative privileges and access rights to enable it!
Caveat: don’t forget to set a (strong)
password for the builtin Administrator account!
Caveat: Windows 10 has the nasty habit
to disable the builtin Administrator account during
updates and upgrades!
Note: the (predefined) privileged user account
NT AUTHORITY\SYSTEM alias
LocalSystem
is always exempt from
Software Restriction Policies;
the (predefined) unprivileged user accounts
NT AUTHORITY\LOCAL SERVICE alias
LocalService
and NT AUTHORITY\NETWORK SERVICE alias
NetworkService
are but subject to them!
Operation
If execution is denied by
Software Restriction Policies,
Win32 functions typically yield error code 1260 alias
ERROR_ACCESS_DISABLED_BY_POLICY
or error code 786 alias
ERROR_ACCESS_DISABLED_NO_SAFER_UI_BY_POLICY,
while Windows’ module loader yields a negative
NTSTATUS
0xC0000361
alias STATUS_ACCESS_DISABLED_BY_POLICY_DEFAULT,
0xC0000362
alias STATUS_ACCESS_DISABLED_BY_POLICY_PATH,
0xC0000363
alias STATUS_ACCESS_DISABLED_BY_POLICY_PUBLISHER,
0xC0000364
alias STATUS_ACCESS_DISABLED_BY_POLICY_OTHER or
0xC0000372
alias STATUS_ACCESS_DISABLED_NO_SAFER_UI_BY_POLICY
respectively.
Note: the Win32 functions
LoadLibrary(),
LoadLibraryEx(),
LoadPackagedLibrary(),
ShellExecute()
and
ShellExecuteEx()
yield error code 5 alias
ERROR_ACCESS_DENIED
instead.
For (portable) executable
files except
DLLs,
one of the messages shown above is displayed and an entry
865,
866,
867,
868
or
882
from source Software Restriction Policies (on
Windows XP, Windows Server 2003 and
Windows Server 2003 R2) or
Microsoft-Windows-SoftwareRestrictionPolicies (on
Windows Vista and newer versions of
Windows NT) is written to the Event Log.
For Windows Installer packages, patches and
transformations, one of the messages shown above is displayed and an
entry
1007
or
1008
from source MsiInstaller is written to the
Event Log.
To retrieve these entries from the Event Log, start the
Command Processor and run (one or more
of) the following command lines:
WMIC.exe NTEvent Where "EventCode='865' Or EventCode='866' Or EventCode='867' Or EventCode='868' Or EventCode='882'" Get /Value
WMIC.exe NTEvent Where "SourceName='Software Restriction Policies'" Get /Value
WMIC.exe NTEvent Where "SourceName='Microsoft-Windows-SoftwareRestrictionPolicies'" Get /Value
WMIC.exe NTEvent Where "(EventCode='1007' Or EventCode='1008') And SourceName='MsiInstaller'" Get /Value
Advanced Logging
All setup scripts turn on Advanced Logging
:
• to the file %SystemRoot%\Debug\SAFER.log
on Windows XP, Windows Server 2003 and
Windows Server 2003 R2;
• to the file
%SystemRoot%\System32\LogFiles\SAFER.log on
Windows Vista and newer versions of
Windows NT.
The NTFS
DACL
of the directories %SystemRoot%\Debug\
and %SystemRoot%\System32\LogFiles\ allow only
privileged users (NT AUTHORITY\SYSTEM
alias
LocalSystem
and members of the
BUILTIN\Administrators group) to
create the file %SystemRoot%\Debug\SAFER.log or
%SystemRoot%\System32\LogFiles\SAFER.log respectively.
The file’s inherited access permissions also allow only
privileged users to write, but unprivileged users
(members of the BUILTIN\Users
group) to read.
On Windows Vista and newer versions of
Windows NT, file and directory operations of 32-bit
applications run by unprivileged users which fail due to missing
write access permissions in %SystemRoot%\ and below as
well as %ProgramFiles%\ and below, on 64-bit editions
also %ProgramFiles(x86)%\ and below, are redirected to
the directory %LOCALAPPDATA%\VirtualStore\, resulting
in
%LOCALAPPDATA%\VirtualStore\Windows\System32\LogFiles\SAFER.log.
Caveat: the file SAFER.log can grow
quite large!
Note: it can be cleared or erased any time.
Availability and Vulnerability
Software Restriction Policies are available
builtin on all editions of
Windows XP and newer versions of
Windows NT.
Note: their successor
AppLocker
is available on Ultimate and Enterprise
editions of Windows 7 and newer versions of
Windows NT only, while Device Guard is
available only on Enterprise editions of
Windows 10 and Windows 11.
Unlike antivirus or other so-called security
software which
is often typically vulnerable itself,
Software Restriction Policies introduce no additional
code which allows to leverage successful attacks in the first place!
Some, but not all (now fixed) vulnerabilities in
Microsoft®’s
anti-malware products for consumers are documented in the
MSKB
articles
932135,
952044,
2823482,
2847927
and
3074162,
the Security Advisories
2491888,
2846338,
2974294,
3074162
and
4022344,
plus the Security Bulletins
MS07-010,
MS08-029,
MS13-034
and
MS13-058.
The additional updates to harden the anti-malware products for
consumers are documented in the
MSKB
articles
2781197,
2856373,
2883200,
2894853,
2939153,
2976536
and
3025417.
Note: so-called security
products of other
vendors are equally bad or even worse!
Analysis and Exploitation of an ESET Vulnerability:
Do we understand the risk vs. benefit trade-offs of security
software?
Tavis Ormandy, June 2015
[…]
Attackers can cause I/O via Web Browsers, Email, IM, file sharing,
network storage, USB, or hundreds of other vectors. Whenever a
message, file, image or other data is received, it’s likely
some untrusted data passes through the disk. Because it’s so
easy for attackers to trigger emulation of untrusted code,
it’s critically important that the emulator is robust and
isolated.
Unfortunately, analysis of ESET emulation reveals that is not the
case and it can be trivially compromised.
Kaspersky: Mo Unpackers, Mo Problems:
Because antivirus products typically intercept filesystem and
network traffic, simply visiting a website or receiving an email is
sufficient for exploitation. It is not necessary to open or read the
email, as the filesystem I/O from receiving the email is sufficient
to trigger the exploitable condition.
[…]
Product Design Flaws
I've also reported some major design flaws in various other
components of Kaspersky Antivirus and Kaspersky Internet Security.
The patches for the remote network attacks I had planned to discuss
here were delayed, and so I'll talk about them in a second post on
this topic once the fixes are live.
Security Software Considered Harmful?
We have strong evidence that an active black market trade in
antivirus exploits exists. Research shows that it’s an easily
accessible attack surface that dramatically increases exposure to
targeted attacks.
How to Compromise the Enterprise Endpoint:
Today we're publishing details of multiple critical vulnerabilities
that we discovered, including many wormable remote code execution
flaws.
These vulnerabilities are as bad as it gets. They don’t
require any user interaction, they affect the default
configuration, and the software runs at the highest privilege levels
possible. In certain cases on Windows, vulnerable code is even
loaded into the kernel, resulting in remote kernel memory
corruption.
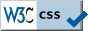
Reliability and Safety
![Screen shot of antivirus software outsmarted by malware via SAFER rules [Screen shot of antivirus software outsmarted by malware via SAFER rules]](https://blog.trendmicro.com/trendlabs-security-intelligence/files/2014/06/blocked.png) On the right, the screen shot of a message box shows antivirus
software which is disabled by
malware (ab)using
Software Restriction Policies, i.e. this antivirus
software was even unable to protect itself!
On the right, the screen shot of a message box shows antivirus
software which is disabled by
malware (ab)using
Software Restriction Policies, i.e. this antivirus
software was even unable to protect itself!
Note:
Self-Protection for Antivirus Software
provides an overview!
Trend Micro: Antivirus industry lied for 20 years:
In the antivirus business, we have been lying to customers for 20
years. People thought that virus protection protected them, but we
can never block all viruses. Antivirus refresh used to be every 24
hours. People would usually get infected in that time and the
industry would clean them up with a new pattern file.
In the last 20 years, we have been misrepresenting ourselves.
No-one is able to detect five and a half million viruses. Nowadays
there are no mass virus outbreaks; [malware] is targeted. But, if
there are no virus samples submitted, there’s no way to detect
them.
Securing That XP Desktop, Part 1:
The best kind of desktop is a secure desktop. As you all know,
hackers are a tricky bunch. You have to go beyond Symantec Antivirus
and actually lock Windows down if you want to make sure your
computing environment is actually secure.
Cyber Resilience And Spear Phishing:
For example, application whitelisting on end-user devices stops
advanced and zero day attacks from infecting the system by
preventing unauthorised code execution, protecting memory, and
blocking attempts to exploit a whitelisted app before it gains a
foothold and impacts the business. Application whitelisting is
listed as a Quick Win in the SANS Critical Security Controls list
and the Australian Government Top 4 Mitigating Controls
cybersecurity guidance. According to Australian Signals Directorate
Deputy Director Steve Day, attackers have not stolen any sensitive
data from government networks because of their adoption of the Top 4
mitigating controls.
How to Mitigate Against Targeted Cyber Intrusion:
But there are very effective protections that you can put in place,
and they need not require new investment in technology or personnel.
The Australian Defence Signals Directorate (DSD) has published
guidance on the top 35 strategies to mitigate against targeted cyber
intrusion and concluded that at least 85 % of the intrusions
they responded to in 2011 and 2012 would have been prevented if only
the top four of these mitigations had been in place.
These top four mitigations only require organizations to employ
application whitelisting technology, maintain current, patched
applications and operating systems and effectively restrict the use
of administrative accounts.
Interoperability and Security
Although Software Restriction Policies work together
with
UAC,
it’s safer to use
Windows is only safe to use with
an unprivileged Standard User account and
strict privilege separation:
One of the common misconceptions about UAC and about Same-desktop
Elevation in particular is that it prevents malware from being
installed or from gaining administrative rights. First, malware can
be written not to require administrative rights, and malware can be
written to write just to areas in the user’s profile. More
important, Same-desktop Elevation in UAC is not a security boundary
and can be hijacked by unprivileged software that runs on the same
desktop. Same-desktop Elevation should be considered a convenience
feature, and from a security perspective,
"Protected Administrator" should be considered the
equivalent of "Administrator." By contrast, using
Fast User Switching to log on to a different session by using an
administrator account involves a security boundary between the
administrator account and the standard user session.
Update on UAC:
One important thing to know is that UAC is not a security boundary.
UAC helps people be more secure, […]
The most effective way to secure a system against malware is to run
with standard user privileges.
Inside Windows 7 User Account Control:
[…] the primary purpose of elevation is not security, though,
it’s convenience: […]
The Long-Term Impact of User Account Control:
[…] this is also where we run into some of the limitations of
UAC. Remember, there is no effective isolation; there is no security
boundary that isolates processes on the same desktop.
Note: as shipped, Windows NT but even
fails to isolate processes running in different sessions, thereby
allowing unprivileged standard users to elevate their privileges to
NT AUTHORITY\SYSTEM alias
LocalSystem!
Inside Windows Vista User Account Control:
It’s important to be aware that UAC elevations are
conveniences and not security boundaries. A security boundary
requires that security policy dictates what can pass through the
boundary. User accounts are an example of a security boundary in
Windows because one user can’t access the data belonging to
another user without having that user’s permission.
The Advantages of Running Applications on Windows Vista:
The UAC’s Administrator Approval Mode, which is the default
configuration, will allow most applications to run in a standard
user mode, even when the user is an administrator. When the
administrator privileges are needed, the UAC prompts the user for
consent. While this is an effective way to reduce the attack
surface, it does not provide the same level of control or security
as using a standard user account.
![Screen shot of default 'User Account Control Settings' from Windows 7 [Screen shot of default 'User Account Control Settings' from Windows 7]](https://support.microsoft.com/library/images/2692682.png) Note: on Windows 7 and newer versions
of Windows NT, with its default setting
UAC performs
silent (automatic) elevation for programs that
Note: on Windows 7 and newer versions
of Windows NT, with its default setting
UAC performs
silent (automatic) elevation for programs that
- have the
autoElevate property set in their (embedded)
Application Manifest,
- are
digitally signed
by Microsoft with the
Windows Publisher
code
signing certificate, and
- are stored in
secure
locations like
%SystemRoot%\ and its subdirectories.
These programs can but trivially be (ab)used by
protected administrators
to write arbitrary files to
write-protected and therefore unrestricted
locations like
%SystemRoot%\ and its subdirectories and thus bypass
NTFS
ACLs,
Software Restriction Policies, and
AppLocker too!
See
UAC-a-mole
alias qUACkery
for some examples, their exploits and the
mitigations.
To prevent the silent (automatic) elevation, set
UAC to its highest
level Always notify
; to prevent any bypass, use a
Standard User account and disable elevation requests
there:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"ConsentPromptBehaviorAdmin"=dword:00000002 ; Prompt for consent on the secure desktop
"ConsentPromptBehaviorUser"=dword:00000000 ; Automatically deny elevation requests
Both policy settings are documented in the
TechNet
article
UAC Group Policy Settings and Registry Key Settings.
Note: according to numbers published by
Microsoft in their
Security Intelligence Reports,
about ½ to ¾ of all (some 600 million)
Windows NT installations engaged in their
malware telemetry
reported only a single active user account.
Google’s
Project Zero
reported several bugs which allow to bypass
UAC that
Microsoft won’t fix:
Issue 156
and
Issue 220.
![Screen shot of message box from 'Windows Explorer' of Windows Vista for granting permanent full access [Screen shot of message box from 'Windows Explorer' of Windows Vista for granting permanent full access]](download/KB950934.PNG) Also note that in combination with
UAC
Windows Explorer shows surprising
and dangerous behaviour (documented in the
MSKB
article
950934)
which generally impairs security and safety!
Also note that in combination with
UAC
Windows Explorer shows surprising
and dangerous behaviour (documented in the
MSKB
article
950934)
which generally impairs security and safety!
To detect directories with additional
NTFS
ACL entries created
by Windows Explorer as well as
(writable) files eventually created in these directories from your
user account, start the
Command Processor, run the following
command lines and inspect their output, then remove the additional
NTFS
ACL entries:
2>NUL: (
ICACLs.exe "%SystemRoot%\*" /FindSID "%USERNAME%" /C /T
ICACLs.exe "%ProgramFiles%\*" /FindSID "%USERNAME%" /C /T
ICACLs.exe "%ProgramFiles(x86)%\*" /FindSID "%USERNAME%" /C /T
ICACLs.exe "%ProgramData%\*" /FindSID "%USERNAME%" /C /T
) | FindStr.exe /B /C:"SID "
ICACLs.exe "‹pathname›" /Remove:g "%USERNAME%"
…
ICACLs.exe "‹pathname›" /Remove:g "%USERNAME%"
To prevent these mishaps to happen again, run the following command
lines as privileged
user administrator to super hide
the
detected directories:
Attrib.exe +H +S "‹directory›"
…
Attrib.exe +H +S "‹directory›"
To detect directories where
Windows Explorer will show this
misbehaviour, run the following command lines as
unprivileged (standard) user:
FOR /D /R "%SystemRoot%" %? IN (*) DO @(DIR "%~?" /A 1>NUL: 2>NUL: || ECHO %?)
FOR /D /R "%ProgramFiles%" %? IN (*) DO @(DIR "%~?" /A 1>NUL: 2>NUL: || ECHO %?)
FOR /D /R "%ProgramFiles(x86)%" %? IN (*) DO @(DIR "%~?" /A 1>NUL: 2>NUL: || ECHO %?)
FOR /D /R "%ProgramData%" %? IN (*) DO @(DIR "%~?" /A 1>NUL: 2>NUL: || ECHO %?)
1>"%TMP%\SAFER.TMP" (
DIR "%SystemRoot%" /A:D /B /S
DIR "%ProgramFiles%" /A:D /B /S
DIR "%ProgramFiles(x86)%" /A:D /B /S
DIR "%ProgramData%" /A:D /B /S)
FOR /F "Delims= UseBackQ" %? IN ("%TMP%\SAFER.TMP") DO @(DIR "%~?" /A 1>NUL: 2>NUL: || ECHO %?)
ERASE "%TMP%\SAFER.TMP"
Prerequisites
Note: these prerequisites are necessary (really:
mandatory) due to deficiencies in
Windows NT!
-
The permission for unprivileged users (really: members of the
NT AUTHORITY\Authenticated Users or
BUILTIN\Users groups) to create
subdirectories in the root directory of the system drive
must
be removed from its
NTFS
ACL to prevent
circumvention of Software Restriction Policies:
ICACLs.exe %SystemDrive%\ /Deny *S-1-5-32-545:(AD,WD) /Remove:d *S-1-5-32-545 /Remove:g *S-1-5-11
-
APPCERT.DLL
must be installed on all versions
of Windows NT to prevent circumvention of
Software Restriction Policies!
-
On Windows 10 and Windows 11 with the
update
4052623
(to be) installed, the corresponding path rule must be uncommented
in the setup script NTX_SAFER.INF before installation.
-
On Windows 10 1709 alias
Fall Creators Update, the update
4093105
fixes the bug that causes Microsoft Edge to stop after
a few seconds.
-
On Windows 10 1703 alias Creators Update,
the update
4093117
fixes the bug that causes Microsoft Edge to stop after
a few seconds.
-
On Windows 7 and Windows Server 2008 R2,
the hotfix
2532445,
the hotfix
2894252,
or the convenience
rollup update
3125574
must be installed to prevent circumvention of
Software Restriction Policies!
-
On Windows 7, Windows Server 2008 R2 and
newer versions of Windows NT, the optional update
977542
should be installed and the following
Registry
entry should be created to prevent unprivileged users from logging
on in Safe Mode
:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"SafeModeBlockNonAdmins"=dword:00000001 ; Disable 'Standard Users' in 'Safe Mode'
-
On Windows Vista and Windows Server 2008,
the optional update
969972
or one of the optional updates
2257986,
2414106
or
2812950
which contain a newer version of the file replaced by
969972
should be installed!
-
On Windows Server 2003 and
Windows Server 2003 R2, the optional update
973825
should be installed!
-
On systems with AMD64 alias x64 processor
architecture running Windows XP,
Windows Server 2003 or
Windows Server 2003 R2, the optional update
942589
must be installed to enable the special directory
pathname %SystemRoot%\SysNative!
Loopholes, Limitations, Dependencies and Bugs
Note: the loopholes, limitations, dependencies and
bugs are imposed from Software Restriction Policies and
their implementation, not the setup scripts!
-
An (unprivileged) adversary who is able to create a directory with
the name of the Windows directory, typically
Windows, followed by a trailing blank and/or with a
file extension of only blanks, in the root directory of the
system drive
, typically C:\, can bypass
Software Restriction Policies on all
versions of Windows due to bugs in the
Win32 functions
FindFirstFile(),
GetFullPathName(),
GetLongPathName()
and
GetShortPathName()
which are called to evaluate path rules!
Note: removing the permission to create
subdirectories in the root directory of the system drive
for
NT AUTHORITY\Authenticated Users and
BUILTIN\Users prevents this
bypass.
-
An (unprivileged) adversary who is able to call the
Win32 functions
CreateProcess(),
CreateProcessAsUser(),
CreateProcessWithLogonW()
and
CreateProcessWithTokenW(),
can bypass Software Restriction Policies on
all versions of Windows!
Note: installation of APPCERT.DLL
prevents this bypass.
Since Software Restriction Policies block the direct
execution of Win32 applications, an adversary needs to
find a way to run code inside one of the trusted Win32
applications installed on a victims computer, which typically means
to (ab)use a vulnerability in these applications and compromise
them.
-
On Windows XP, Windows Server 2003,
Windows Server 2003 R2,
Windows Embedded POSReady 2009,
Windows Embedded Standard 2009,
Windows Vista and Windows Server 2008,
Software Restriction Policies can be bypassed: the
hotfixes
2532445
and
2894252
are not available for these versions of Windows NT!
Note: an adversary must but be able to call the
Win32 function
LoadLibraryEx()
to exercise this bypass.
Since Software Restriction Policies block the direct
execution of Win32 applications, an adversary needs to
find a way to run code inside one of the trusted Win32
applications installed on a victims computer, which typically means
to (ab)use a vulnerability in these applications and compromise
them.
-
On Windows XP,
Windows Embedded POSReady 2009 and
Windows Embedded Standard 2009, hash rules are not
applied to DLLs.
Note: this limitation is documented in the
MSKB
article
310791.
-
On Windows 8 and later versions, registry path rules
are not (properly) evaluated, especially in
Modern Apps
as well as Universal Windows Apps
.
-
Certificate rules are not applied to
DLLs!
-
Path rules with more than 133 character long paths are
silently ignored!
-
Rules defined with the nil
GUID
{00000000-0000-0000-0000-000000000000} are silently
ignored!
- Software Restriction Policies control the execution of
- Win32 applications loaded via the Win32
functions
CreateProcess(),
CreateProcessAsUser(),
CreateProcessWithLogonW(),
CreateProcessWithTokenW(),
LoadModule()
and
WinExec(),
independent of their file extension,
- DLLs
loaded via the Win32 functions
LoadLibrary(),
LoadLibraryEx()
and
LoadPackagedLibrary(),
independent of their file extension,
- files launched via the Win32 functions
ShellExecute()
and
ShellExecuteEx(),
depending on their file extension,
i.e. all Win32 functions that load and execute
Win32 portable executables
or open files for
execution.
-
Unless disabled with the following
Registry
entry,
Software Restriction Policies control the execution of
scripts interpreted and run by the
Windows Script Host,
independent of their file extension:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings]
"UseWINSAFER"="0"
-
Software Restriction Policies control the installation
of Windows Installer packages and patches.
-
Software Restriction Policies don’t control the
execution of MS-DOS and 16-bit
Windows applications: these run inside the
NTVDM alias
WOWEXEC subsystem,
available only on systems with I386 alias
x86 processor architecture.
To disable the
NTVDM and the
WOWEXEC subsystem,
set the Registry entry
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\AppCompat]
"VDMDisallowed"=dword:00000001
documented in the Security Advisory
979682
and the Security Bulletin
MS13-063,
plus the Registry entry
REGEDIT4
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\WoW]
"DisallowedPolicyDefault"=dword:00000001
documented in the Security Bulletin
MS10-098.
-
Software Restriction Policies don’t control the
execution of
OS/2 or
POSIX
applications: these run inside their own optional and separate
OS/2 or
POSIX
subsystem, either
SFU
(available for Windows XP and
Windows Server 2003) or
SUA
(available for or included as Optional Component in
Windows Server 2003 R2, Windows Vista,
Windows Server 2008, Windows 7,
Windows Server 2008 R2, Windows 8 and
Windows Server 2012, but deprecated).
-
Software Restriction Policies don’t control the
interpretation and execution of code, macros or scripts inside
Win32 applications unless these explicitly call the
Win32 functions that implement
SAFER:
- the Windows Script Component Runtime, implemented in
SCRObj.dll,
called for example via
RegSvr32.exe,
can run arbitrary
Windows Script Components
alias
Scriptlets,
i.e.
COM
objects written in
JScript,
VBScript
or any other scripting language supported by an installed
Windows Script Engine;
- PowerShell
can run arbitrary scripts from its command line, can call arbitrary
methods of the .NET runtime, can call arbitrary
Win32 functions, can instantiate and call arbitrary
COM
objects;
- a Java runtime engine can run arbitrary applets;
- an Office Suite can run arbitrary macros;
- a WWW browser, a
Mail client, an Instant Messenger or a
PDF viewer can
run arbitrary JavaScript;
- a Flash Player can run arbitrary
ActionScript;
- …
Note: use the policies and settings of the
respective host application to control its execution behaviour!
For Internet Explorer for example,
the MSKB
articles
883256
and
915729
document how to disable execution of scripts.
Note: the almost identical limitations and
dependencies of AppLocker are documented in the
TechNet
article
Security Considerations for AppLocker.
Details
![Screen shot of 'Designated File Types Properties' from Windows Vista [Screen shot of 'Designated File Types Properties' from Windows Vista]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure03(en-us,technet.10).jpg) Subject to Software Restriction Policies are files that
match the definition of
Subject to Software Restriction Policies are files that
match the definition of executable
:
- Win32
portable executables
, i.e. applications
and DLLs,
independent of their file extension, typically .exe,
.com, .scr, .dll,
.cpl, .ocx, .ime,
.mui, .ax, .acm,
.vcm, .tsp, .sys,
.rll, .wll, .xll,
.efi, …;
- packages, patches and transformations for the
Windows Installer, previously known as
Microsoft Installer (
.msi,
.msp and .mst);
- scripts for the Windows Script Host, independent of
their file extension, typically
.js,
.jse, .vb, .vbs,
.vbe, .ws, .wsc,
.wsf, .wsh, …;
- COM scriptlets
(
.sct);
- PowerShell scripts and modules (
.ps1 and
.psm1);
- batch scripts (
.bat and .cmd), independent
of their file extension;
- setup scripts (
.inf);
- HTML
applications (
.hta and .htc);
- …
See the documentation for the Win32 functions
SaferiIsExecutableFileType()
and
AssocIsDangerous()
for details.
Windows’ module loader, the Win32
functions CreateProcess*(),
WinExec(),
LoadModule(),
LoadLibrary*() and
LoadPackagedLibrary(),
the Windows Installer, the
Windows Script Host, the PowerShell
interpreter and the Command Processor
call the SAFER functions for every file they open for
execution; only the
Windows Explorer, i.e. the
Win32 functions ShellExecute*(),
evaluates the list of Designated File Types
and calls the
SAFER functions when a file extension matches.
Except on Home and Starter editions of
Windows NT, this list of file extensions can be viewed
and modified via the
Local Security Policy
snap-in of the
Microsoft Management Console.
Note: the predefined list of file extensions is
almost identical to the Unsafe File List
of
Internet Explorer, documented in
the MSKB
article
291369.
![Screen shot of 'Local Security Policy' snap-in from Windows Vista [Screen shot of 'Local Security Policy' snap-in from Windows Vista]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure13(en-us,technet.10).jpg) Caveat: the
Local Security Policy snap-in reads
SAFER settings and rules only from the file
Caveat: the
Local Security Policy snap-in reads
SAFER settings and rules only from the file
%SystemRoot%\System32\GroupPolicy\Machine\Registry.pol,
not from the Registry; SAFER settings and
rules written directly and only to the Registry
therefore don’t show in the
Local Security Policy snap-in!
If this file exists, modifications of the SAFER
settings or rules written directly and only to the
Registry will (periodically) be overwritten with the
SAFER settings and rules from the file!
If this file contains neither SAFER settings nor rules
(or does not exist), the
Local Security Policy snap-in
(creates it and) writes the default SAFER settings and
rules to the file and to the
Registry, thereby overwriting existing
SAFER settings and rules in the Registry!
To avoid this, either run the program SRP2LGPO.EXE
(available upon
request)
once to export all SAFER settings and
rules from the Registry to the file
%SystemRoot%\System32\GroupPolicy\Machine\Registry.pol,
download the (empty
)
REGISTRY.POL
REGISTRY.POL
that contains the (missing) setting
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers]
"Levels"=dword:00071000
which enables all SAFER security levels and save it as
%SystemRoot%\System32\GroupPolicy\Machine\Registry.pol,
or create it from scratch:
COPY CON: "%TMP%\SAFER.TMP"
50 52 65 67 01 00 00 00 5b 00 53 00 4f 00 46 00 PReg....[.S.O.F.
54 00 57 00 41 00 52 00 45 00 5c 00 50 00 6f 00 T.W.A.R.E.\.P.o.
6c 00 69 00 63 00 69 00 65 00 73 00 5c 00 4d 00 l.i.c.i.e.s.\.M.
69 00 63 00 72 00 6f 00 73 00 6f 00 66 00 74 00 i.c.r.o.s.o.f.t.
5c 00 57 00 69 00 6e 00 64 00 6f 00 77 00 73 00 \.W.i.n.d.o.w.s.
5c 00 53 00 61 00 66 00 65 00 72 00 5c 00 43 00 \.S.a.f.e.r.\.C.
6f 00 64 00 65 00 49 00 64 00 65 00 6e 00 74 00 o.d.e.I.d.e.n.t.
69 00 66 00 69 00 65 00 72 00 73 00 00 00 3b 00 i.f.i.e.r.s...;.
4c 00 65 00 76 00 65 00 6c 00 73 00 00 00 3b 00 L.e.v.e.l.s...;.
04 00 00 00 3b 00 04 00 00 00 3b 00 00 10 07 00 ....;.....;.....
5d 00 ].
^Z
CertUtil.exe /DecodeHex /V "%TMP%\SAFER.TMP" "%SystemRoot%\System32\GroupPolicy\Machine\Registry.pol"
ERASE "%TMP%\SAFER.TMP"
1 file(s) copied.
Input Length = 734
Output Length = 162
CertUtil: -decodehex command completed successfully.
Note: for details see the
MSDN article
Registry Policy File Format.
Note: if the file
%SystemRoot%\System32\GroupPolicy\Machine\Registry.pol
is hidden, the Local Security Policy
snap-in fails and displays a (bogus) error message
access denied
when applying changes!
Background Information
More than 25 years ago Microsoft introduced the
NTFS file
system supporting fine-grained
ACLs to control
access to file system objects and
User Profiles
to separate user data (with emphasis on
data
) from each other as well as from the operating system.
More than 15 years ago Microsoft introduced
Software Restriction Policies
alias
SAFER
and published the
MSDN articles
Using Software Restriction Policies to Protect Against Unauthorized Software
Using Software Restriction Policies to Protect Against Unauthorized Software,
Using Software Restriction Policies to Protect Against Unauthorized Software
and
How Software Restriction Policies Work
�
Note:
�
�
�
�:
�
From
Strategies to Mitigate Cyber Security Incidents:
At least 85 % of the adversary techniques used in targeted
cyber intrusions which
ASD has
visibility of could be mitigated by implementing the following
mitigation strategies, referred to as the 'Top 4':
• use application whitelisting to help prevent malicious
software and unapproved programs from running
[…]
�
From
NCSC Applocker Guidance:
Application whitelisting is one of the best available protections against malware.
�
More than 15 years ago Microsoft introduced
DEP
alias
W^X
and enabled it by default.
�
But even today all (data) files created in the
User Profiles, the %PUBLIC%\,
%ProgramData%\ and almost all other data
directories too are still executable: although not
needed the (inheritable)
NTFS
ACLs of all these
directories include execute
permission for files!
And Software Restriction Policies are still not enabled
by default!
�
The immediate benefit of an
NTFS
ACL without
execute
permission or the default SAFER ruleset
is: no (unintended) execution of files like
invoice.pdf.exe etc. stored in data
directories,
so spreading
malware to
Windows NT systems becomes utterly useless.
If you want to try
DEP in the
NTFS
filesystem
for yourself, choose one of the following:
- Add the NTFS
ACL entry
(D;OIIO;WP;;;WD)
meaning
deny execution of files in this directory for everyone, inheritable to all files in all subdirectories
for your own %USERPROFILE%\ directory (or all of them
plus %ALLUSERSPROFILE%\ alias
%ProgramData%\ and %PUBLIC%\ if you have
administrative privileges).
Note: deny
ACL entries have
precedence over allow
ACL entries.
- Enable the default SAFER ruleset which allows execution
(of
*.exe) only in the directories
%SystemRoot%\ and %SystemRoot%\System32\
and all executable files in the directory
%ProgramFiles%\ and below.
Note: this ruleset leaves but many
loopholes!
On systems with AMD64 alias x64
processor architecture, add path rules to allow execution of
%SystemRoot%\SysWoW64\*.exe and
%SystemRoot%\Sysnative\*.exe as well as
%ProgramFiles(x86)%\.
Note: without these additional rules, applications
can’t execute applications for the other
processor
architecture!
-
Follow the step-by-step instructions presented on
How to make a disallowed-by-default Software Restriction Policy.
Note: these instructions let
Windows Apps (which were introduced with
Windows 8) fail and leave multiple loopholes!
-
Download and install the setup script
XP_SAFER.INF
(for Windows XP, including embedded editions,
Windows Server 2003 and
Windows Server 2003 R2),
NT6_SAFER.INF
(for Windows Vista and Windows 7 as well
as Windows Server 2008 and
Windows Server 2008 R2) or
NTX_SAFER.INF
(for Windows 8, Windows 8.1,
Windows 10 and Windows 11 as well as
Windows Server 2012,
Windows Server 2012 R2,
Windows Server 2016, Windows Server 2019
and Windows Server 2022) respectively.
Then open the SPAM folder of your mail client, get one
of the many invoice.pdf.exe your anti-virus software
fails to detect and Open
it.
Fallacies, Misconceptions and Myths
SAFER has to be installed.
Software Restriction Policies alias SAFER
are a builtin feature of Windows XP
and newer versions of Windows NT!
SAFER is not available in Home
editions.
SAFER is available in all editions of
Windows XP and newer versions of
Windows NT!
Home and Starter editions only lack the
Local Security Policy snap-in of the
Microsoft Management Console.
SAFER is not suited for ordinary users.
The SAFER ruleset configured by the setup scripts
XP_SAFER.INF, NT6_SAFER.INF and
NTX_SAFER.INF is made especially for
ordinary (unprivileged alias standard) users who work with the
applications installed on their computers!
SAFER needs constant maintenance.
The SAFER ruleset configured by the setup scripts
XP_SAFER.INF, NT6_SAFER.INF and
NTX_SAFER.INF allows to run all
properly installed applications which meet the
minimum requirements of the more than 25 years old
Designed for Windows guidelines!
I use UAC, I
don’t need SAFER.
UAC does
not protect against execution of programs which run
with standard user rights, for example ransomware
like
Locky
!
SAFER locks me out of my computer.
The SAFER ruleset configured by the setup scripts
XP_SAFER.INF, NT6_SAFER.INF and
NTX_SAFER.INF restricts unprivileged users only, but
not administrators, and does not restrict applications shipped with
Windows NT!
Additionally, Software Restriction Policies are
not active in Safe Mode
, where they can be
disabled, for example via
Registry Editor:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers]
;"PolicyScope"=dword:00000001 ; exempt 'Administrators'
"TransparentEnabled"=dword:00000000 ; no enforcement
Implementation and Build Details
The SAFER ruleset configured by the setup scripts
NTX_SAFER.INF, NT6_SAFER.INF,
XP_SAFER.INF, NT6_SUPER.INF and
XP_SUPER.INF uses a
belt & suspenders
approach: although the
Default rule denies execution, additional
Disallowed rules are defined for almost all paths and
directories except %SystemRoot%\,
%ProgramFiles%\ and %ProgramFiles(x86)%\,
i.e. all local drives, all network paths,
%ProgramData%\, %PUBLIC%\,
%ALLUSERSPROFILE%\, %USERPROFILE%\,
%TEMP%\, %TMP%\ etc.
All SAFER registry path rules which allow execution
reference only Registry entries below
HKEY_LOCAL_MACHINE to prevent users from tampering.
Note: never define a SAFER path rule
that allows execution and references an environment variable or a
Registry entry a user can write or modify!
SRP2LGPO.EXE, the program to export SAFER
settings and rules from the Registry to the file
%SystemRoot%\System32\GroupPolicy\Machine\Registry.pol,
is a pure Win32 application, written in
ANSI C,
built with the Platform
SDK for
Windows Server 2003 R2
Microsoft Visual C++ Compiler 2010 SP1 from update
2519277,
but without the
MSVCRT
libraries, for use on Windows 2000 and newer versions
of Windows NT.
SRP2LGPO.EXE is available for the I386
alias x86, AMD64 alias x64
and IA64 processor architectures of
Windows NT.
Download
Download (one of) the setup scripts
XP_SAFER.INF,
XP_SUPER.INF,
NT6_SAFER.INF,
NT6_SUPER.INF
or
NTX_SAFER.INF
suitable for your version of Windows NT, and optionally
the file
REGISTRY.POL.
Installation
Creating INF Files for Multiple Platforms and Operating Systems
Installation requires administrative privileges and access rights.
Right-click the downloaded setup script *_SAFER.INF to
display its context menu and click Install
to run the
installation.
Note: on systems with AMD64 alias
x64 processor architecture, the installation
must be run in the native (64-bit) execution
environment!
Note: on Windows Vista and newer
versions of Windows NT,
InfDefaultInstall.exe,
the application registered for the Install
verb of
*.inf files, requests administrative privileges.
Test
Perform the following 5 simple steps to verify the successful
activation of Software Restriction Policies and to
detect user-writable subdirectories beneath
%SystemRoot%\, %ProgramFiles%\ and
%ProgramFiles(x86)%\ missed by the SAFER
ruleset.
Note: the SAFER ruleset denies
execution in all user-writable directories of default installations
of Windows.
-
Log on to an unprivileged (standard) user account if possible, else
to the user protected administrator
account created during Windows Setup.
-
Right click on the desktop background to display the context menu,
select New
, then Text Document
; change the file
extension .txt to .cmd and press the
Enter key.
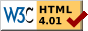
![Screen shot of message box from 'Windows Explorer' of Windows Vista for blocked program [Screen shot of message box from 'Windows Explorer' of Windows Vista for blocked program]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure15(en-us,technet.10).jpg) Press the Enter key again to execute the
just created (empty) batch script, or open it per double-click: a
message box like that shown to the right must be displayed!
Press the Enter key again to execute the
just created (empty) batch script, or open it per double-click: a
message box like that shown to the right must be displayed!
-
Start the Command Processor and run the
following command lines to enumerate all (sub)directories beneath
%SystemRoot%\, %ProgramFiles%\ and
%ProgramFiles(x86)%\, attempt to create a (hardlink of
the) batch script SAFER.BAT in each of them and (try to)
execute it, attempt to create an Alternate Data Stream
SAFER.VBS on each of them and (try to) execute it,
logging the pathnames of directories where execution succeeds to the
file %TMP%\SAFER.LOG:
REM Copyright © 2004-2024, Stefan Kanthak <stefan.kanthak@nexgo.de>
ECHO @ECHO %~dp0 1>"%TMP%\SAFER.TMP"
MOVE "%TMP%\SAFER.TMP" "%SystemRoot%\Temp\SAFER.TMP" && (
COPY NUL: "%TMP%\SAFER.LOG" && (
DIR "%ProgramFiles%" /A:D /B /S 1>"%TMP%\SAFER.TMP"
IF DEFINED ProgramFiles(x86) IF NOT "%ProgramFiles(x86)%" == "%ProgramFiles%" (
DIR "%ProgramFiles(x86)%" /A:D /B /S 1>>"%TMP%\SAFER.TMP")
DIR "%SystemRoot%" /A:D /B /S 1>>"%TMP%\SAFER.TMP"
FOR /F "Delims= UseBackQ" %? IN ("%TMP%\SAFER.TMP") DO @(
MKLINK /H "%~?\SAFER.BAT" "%SystemRoot%\Temp\SAFER.TMP" 2>NUL: && (
CALL "%~?\SAFER.BAT" 1>>"%TMP%\SAFER.LOG"
ERASE "%~?\SAFER.BAT")
ECHO WScript.Echo WScript.ScriptFullName 1>"%~?:SAFER.VBS" && (
"%SystemRoot%\System32\CSCRIPT.EXE" //NOLOGO "%~?:SAFER.VBS" 1>>"%TMP%\SAFER.LOG"))
ERASE "%SystemRoot%\Temp\SAFER.TMP"
ERASE "%TMP%\SAFER.TMP"
TYPE "%TMP%\SAFER.LOG"))
Note: the command lines can be copied and pasted as
block into a Command Processor window!
Caveat: the command lines can but detect
user-writable directories only in paths where access permissions
allow to list their contents!
1 file(s) moved.
1 file(s) copied.
Hardlink created for C:\Windows\Tasks\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\Temp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\Temp\SAFER.BAT
Hardlink created for C:\Windows\Tracing\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\debug\WIA\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\Registration\CRMLog\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\System32\FxsTmp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\System32\Tasks\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\System32\Tasks\SAFER.BAT
Hardlink created for C:\Windows\System32\catroot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\System32\com\dmp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\System32\com\dmp\SAFER.BAT
Hardlink created for C:\Windows\System32\Spool\Printers\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\System32\Spool\Printers\SAFER.BAT
Hardlink created for C:\Windows\System32\Spool\Drivers\color\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\SysWOW64\FxsTmp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\SysWOW64\Tasks\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\SysWOW64\Tasks\SAFER.BAT
Hardlink created for C:\Windows\SysWOW64\com\dmp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\SysWOW64\com\dmp\SAFER.BAT
ERASE "C:\Windows\Temp\SAFER.TMP"
Could Not Find C:\Windows\Temp\SAFER.TMP
Caveat: due to unnecessary access
permissions requested by the builtin ERASE command the
deletion of (the hardlink) SAFER.BAT fails in multiple
user-writable directories; run the following command line to list
the left-over files:
FSUtil.exe HARDLINK LIST "%SystemRoot%\Temp\SAFER.TMP"
Caveat: Alternate Data Streams can
unfortunately not be deleted with the builtin ERASE
command!
-
Create the text file SAFER.CMD with the following
content in an arbitrary directory on the system drive
%SystemDrive%\ where execution is allowed, for example
the Windows directory %SystemRoot%\:
REM Copyright © 2004-2024, Stefan Kanthak <stefan.kanthak@nexgo.de>
SET DATE=
DATE %DATE% 2>NUL:
IF NOT ERRORLEVEL 1 EXIT /B
ECHO @ECHO %%~dp0 1>"%TMP%\SAFER.TMP"
MOVE "%TMP%\SAFER.TMP" "%SystemRoot%\Temp\SAFER.TMP"
IF ERRORLEVEL 1 EXIT /B
COPY NUL: "%TMP%\SAFER.LOG"
IF ERRORLEVEL 1 EXIT /B
"%SystemRoot%\System32\MODE.COM" CON: LINES=9999
DIR "%ProgramFiles%" /A:D /B /S 1>"%TMP%\SAFER.TMP"
IF DEFINED ProgramFiles(x86) IF NOT "%ProgramFiles(x86)%" == "%ProgramFiles%" (
DIR "%ProgramFiles(x86)%" /A:D /B /S 1>>"%TMP%\SAFER.TMP")
DIR "%SystemRoot%" /A:D /B /S 1>>"%TMP%\SAFER.TMP"
FOR /F "Delims= UseBackQ" %%? IN ("%TMP%\SAFER.TMP") DO @(
MKLINK /H "%%~?\SAFER.BAT" "%SystemRoot%\Temp\SAFER.TMP" 2>NUL: && (
CALL "%%~?\SAFER.BAT" 1>>"%TMP%\SAFER.LOG"
ERASE "%%~?\SAFER.BAT")
ECHO WScript.Echo WScript.ScriptFullName 1>"%%~?:SAFER.VBS" && (
"%SystemRoot%\System32\CSCRIPT.EXE" //NOLOGO "%%~?:SAFER.VBS" 1>>"%TMP%\SAFER.LOG"))
ERASE "%SystemRoot%\Temp\SAFER.TMP"
ERASE "%TMP%\SAFER.TMP"
TYPE "%TMP%\SAFER.LOG"
EXIT /B
The batch script
SAFER.CMD
enumerates all (sub)directories beneath %SystemRoot%\,
%ProgramFiles%\ and %ProgramFiles(x86)%\,
attempts to create a (hardlink of the secondary) batch script
SAFER.BAT in each of them and (tries to) execute it,
attempts to create an Alternate Data Stream
SAFER.VBS on each of them and (tries to) execute it,
logging the pathnames of directories where execution succeeds to the
file %TMP%\SAFER.LOG.
Caveat: the batch script SAFER.CMD
can but detect user-writable directories only in paths where access
permissions allow to list their contents!
-
Execute the batch script SAFER.CMD created in the
previous step per double-click:
REM Copyright © 2004-2024, Stefan Kanthak <stefan.kanthak@nexgo.de>
DATE 08/15/2009 2>NUL:
IF NOT ERRORLEVEL 1 EXIT /B
ECHO @ECHO %~dp0 1>"C:\Users\Stefan\AppData\Local\Temp\SAFER.TMP"
MOVE "C:\Users\Stefan\AppData\Local\Temp\SAFER.TMP" "C:\Windows\Temp"
1 file(s) moved.
IF ERRORLEVEL 1 EXIT /B
COPY NUL: "C:\Users\Stefan\AppData\Local\Temp\SAFER.LOG"
1 file(s) copied.
IF ERRORLEVEL 1 EXIT /B
DIR "C:\Program Files" /A:D /B /S 1>"C:\Users\Stefan\AppData\Local\Temp\SAFER.TMP"
IF DEFINED ProgramFiles(x86) IF NOT "C:\Program Files (x86)" == "C:\Program Files" (
DIR "C:\Program Files (x86)" /A:D /B /S 1>>"C:\Users\Stefan\AppData\Local\Temp\SAFER.TMP")
DIR "C:\Windows" /A:D /B /S 1>>"C:\Users\Stefan\AppData\Local\Temp\SAFER.TMP"
FOR /F "Delims= UseBackQ" %? IN ("C:\Users\Stefan\AppData\Local\Temp\SAFER.TMP") DO @(
Hardlink created for C:\Windows\Tasks\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\Temp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\Temp\SAFER.BAT
Hardlink created for C:\Windows\Tracing\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\debug\WIA\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\Registration\CRMLog\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\System32\FxsTmp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\System32\Tasks\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\System32\Tasks\SAFER.BAT
Hardlink created for C:\Windows\System32\catroot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\System32\com\dmp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\System32\com\dmp\SAFER.BAT
Hardlink created for C:\Windows\System32\Spool\Printers\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\System32\Spool\Printers\SAFER.BAT
Hardlink created for C:\Windows\System32\Spool\Drivers\color\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\SysWOW64\FxsTmp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Hardlink created for C:\Windows\SysWOW64\Tasks\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\SysWOW64\Tasks\SAFER.BAT
Hardlink created for C:\Windows\SysWOW64\com\dmp\SAFER.BAT <<===>> C:\Windows\Temp\SAFER.TMP
This program is blocked by group policy. For more information, contact your system administrator.
Could Not Find C:\Windows\SysWOW64\com\dmp\SAFER.BAT
ERASE "C:\Windows\Temp\SAFER.TMP"
Could Not Find C:\Windows\Temp\SAFER.TMP
ERASE "C:\Users\Stefan\AppData\Local\Temp\SAFER.TMP"
TYPE "C:\Users\Stefan\AppData\Local\Temp\SAFER.LOG"
EXIT /B
Caveat: due to unnecessary access
permissions requested by the builtin ERASE command the
deletion of (the hardlink) SAFER.BAT fails in multiple
user-writable directories; run the following command line to list
the left-over files:
FSUtil.exe HARDLINK LIST "%SystemRoot%\Temp\SAFER.TMP"
Caveat: Alternate Data Streams can
unfortunately not be deleted with the builtin ERASE
command!
-
Open the file SAFER.LOG created in your
%TMP% directory %LOCALAPPDATA%\Temp\ alias
%USERPROFILE%\AppData\Local\Temp\: if it is
not empty then either remove the user-writable
directories listed there or add path rules to deny execution.
-
Create the text file SAFER.C with the following
content in an arbitrary, preferable empty directory:
// Copyright © 2004-2024, Stefan Kanthak <stefan.kanthak@nexgo.de>
#define STRICT
#define UNICODE
#define WIN32_LEAN_AND_MEAN
#include <windows.h>
#include <winsafer.h>
#include <wintrust.h>
#if ANYSIZE_ARRAY != 1
#error ANYSIZE_ARRAY must be defined as 1!
#endif
#define wmemcpy __movsw
__declspec(safebuffers)
BOOL CDECL PrintConsole(HANDLE hConsole, [SA_FormatString(Style="printf")] LPCWSTR lpFormat, ...)
{
WCHAR szOutput[1024];
DWORD dwOutput;
DWORD dwConsole;
va_list vaInput;
va_start(vaInput, lpFormat);
dwOutput = wvsprintf(szOutput, lpFormat, vaInput);
va_end(vaInput);
if (dwOutput == 0)
return FALSE;
if (!WriteConsole(hConsole, szOutput, dwOutput, &dwConsole, NULL))
return FALSE;
return dwConsole == dwOutput;
}
WCHAR szPathName[32768] = L"";
const SAFER_CODE_PROPERTIES scp = {sizeof(scp),
SAFER_CRITERIA_AUTHENTICODE | SAFER_CRITERIA_IMAGEHASH | SAFER_CRITERIA_IMAGEPATH,
szPathName,
(HANDLE) NULL,
0,
{0},
0,
{0},
(ALG_ID) 0,
(LPBYTE) NULL,
HWND_DESKTOP,
WTD_UI_NONE};
DWORD WINAPI SRPLevel(HANDLE hConsole)
{
SAFER_LEVEL_HANDLE slh = INVALID_HANDLE_VALUE;
DWORD dwLevelId = ~0UL;
DWORD dw;
if (!SaferIdentifyLevel(1, &scp, &slh, NULL))
PrintConsole(hConsole,
L"SaferIdentifyLevel() returned error %lu for path \'%ls\'\n",
GetLastError(), scp.ImagePath);
else
{
if (!SaferGetLevelInformation(slh, SaferObjectLevelId, &dwLevelId, sizeof(dwLevelId), &dw))
PrintConsole(hConsole,
L"SaferGetLevelInformation() returned error %lu for path \'%ls\'\n",
GetLastError(), scp.ImagePath);
if (!SaferCloseLevel(slh))
PrintConsole(hConsole,
L"SaferCloseLevel() returned error %lu\n",
GetLastError());
}
return dwLevelId;
}
typedef struct _ace
{
ACE_HEADER header;
ACCESS_MASK mask;
SID trustee;
} ACE;
const struct _acl
{
ACL acl;
ACE ace[ANYSIZE_ARRAY];
} dacl = {{ACL_REVISION, 0, sizeof(dacl), ANYSIZE_ARRAY, 0},
#if 0 // (A;NP;0x1f0000;;;AU)
{{{ACCESS_ALLOWED_ACE_TYPE, NO_PROPAGATE_INHERIT_ACE, sizeof(ACE)},
STANDARD_RIGHTS_ALL,
{SID_REVISION, ANYSIZE_ARRAY, SECURITY_NT_AUTHORITY, SECURITY_AUTHENTICATED_USER_RID}}}};
#else // (A;NP;0x1f0000;;;OW)
{{{ACCESS_ALLOWED_ACE_TYPE, NO_PROPAGATE_INHERIT_ACE, sizeof(ACE)},
STANDARD_RIGHTS_ALL,
{SID_REVISION, ANYSIZE_ARRAY, SECURITY_CREATOR_SID_AUTHORITY, SECURITY_CREATOR_OWNER_RIGHTS_RID}}}};
#endif
const SECURITY_DESCRIPTOR sd = {SECURITY_DESCRIPTOR_REVISION,
0,
SE_DACL_PRESENT | SE_DACL_PROTECTED | SE_GROUP_DEFAULTED | SE_OWNER_DEFAULTED | SE_SACL_DEFAULTED,
(SID *) NULL,
(SID *) NULL,
(ACL *) NULL,
&dacl};
const SECURITY_ATTRIBUTES sa = {sizeof(sa),
&sd,
FALSE};
__declspec(safebuffers)
DWORD WINAPI Traverse(HANDLE hConsole, DWORD dwPathName)
{
DWORD dwFileName;
DWORD dwError = ERROR_SUCCESS;
LPWSTR lpPathName = szPathName + dwPathName;
HANDLE hFindFile;
HANDLE hStream;
DWORD dwStream = 0;
HANDLE hFile;
DWORD dwFile = 0;
WIN32_FIND_DATA wfd;
#if 0
wcscpy(lpPathName, L":SAFER.TMP");
#else
wmemcpy(lpPathName, L":SAFER.TMP", sizeof(":SAFER.TMP"));
#endif
hStream = CreateFile(szPathName,
FILE_WRITE_DATA,
FILE_SHARE_DELETE | FILE_SHARE_READ | FILE_SHARE_WRITE,
(LPSECURITY_ATTRIBUTES) NULL,
CREATE_ALWAYS,
#if 0 // NOTE: FILE_FLAG_DELETE_ON_CLOSE requires DELETE access and permission!
FILE_FLAG_DELETE_ON_CLOSE,
#elif 0
FILE_ATTRIBUTE_TEMPORARY,
#else
FILE_ATTRIBUTE_NORMAL,
#endif
(HANDLE) NULL);
if (hStream != INVALID_HANDLE_VALUE)
{
if (!WriteFile(hStream,
L"\xFEFF", // UTF-16LE byte order mark
sizeof(L'\xFEFF'),
&dwStream,
(LPOVERLAPPED) NULL))
PrintConsole(hConsole,
L"WriteFile() returned error %lu for alternate data stream \'%ls\'\n",
GetLastError(), szPathName);
else
if (dwStream != sizeof(L'\xFEFF'))
PrintConsole(hConsole,
L"WriteFile() failed, %lu of %lu bytes written to alternate data stream \'%ls\'\n",
dwStream, sizeof(L'\xFEFF'), szPathName);
else
PrintConsole(hConsole,
L"%lu\t%ls\n",
SRPLevel(hConsole), szPathName);
if (!CloseHandle(hStream))
PrintConsole(hConsole,
L"CloseHandle() returned error %lu\n",
GetLastError());
if (!DeleteFile(szPathName))
PrintConsole(hConsole,
L"DeleteFile() returned error %lu for alternate data stream \'%ls\'\n",
GetLastError(), szPathName);
}
else
{
dwError = GetLastError();
if (dwError != ERROR_ACCESS_DENIED)
PrintConsole(hConsole,
L"CreateFile() returned error %lu for alternate data stream \'%ls\'\n",
dwError, szPathName);
else
dwError = ERROR_SUCCESS;
}
#if 0
wcscpy(lpPathName, L"\\SAFER.TMP");
#elif 0
wmemcpy(lpPathName, L"\\SAFER.TMP", sizeof("\\SAFER.TMP"));
#else
lpPathName[0] = L'\\';
#endif
hFile = CreateFile(szPathName,
FILE_WRITE_DATA,
FILE_SHARE_DELETE | FILE_SHARE_READ | FILE_SHARE_WRITE,
#if 0
(LPSECURITY_ATTRIBUTES) NULL,
#else
&sa,
#endif
CREATE_ALWAYS,
#if 0 // NOTE: FILE_FLAG_DELETE_ON_CLOSE requires DELETE access and permission!
FILE_FLAG_DELETE_ON_CLOSE,
#elif 0
FILE_ATTRIBUTE_TEMPORARY,
#else
FILE_ATTRIBUTE_NORMAL,
#endif
(HANDLE) NULL);
if (hFile != INVALID_HANDLE_VALUE)
{
if (!WriteFile(hFile,
L"\xFEFF", // UTF-16LE byte order mark
sizeof(L'\xFEFF'),
&dwFile,
(LPOVERLAPPED) NULL))
PrintConsole(hConsole,
L"WriteFile() returned error %lu for file \'%ls\'\n",
GetLastError(), szPathName);
else
if (dwFile != sizeof(L'\xFEFF'))
PrintConsole(hConsole,
L"WriteFile() failed, %lu of %lu bytes written to file \'%ls\'\n",
dwFile, sizeof(L'\xFEFF'), szPathName);
else
PrintConsole(hConsole,
L"%lu\t%ls\n",
SRPLevel(hConsole), szPathName);
if (!CloseHandle(hFile))
PrintConsole(hConsole,
L"CloseHandle() returned error %lu\n",
GetLastError());
if (!DeleteFile(szPathName))
PrintConsole(hConsole,
L"DeleteFile() returned error %lu for file \'%ls\'\n",
GetLastError(), szPathName);
}
else
{
dwError = GetLastError();
if (dwError != ERROR_ACCESS_DENIED)
PrintConsole(hConsole,
L"CreateFile() returned error %lu for file \'%ls\'\n",
dwError, szPathName);
else
dwError = ERROR_SUCCESS;
if (CreateDirectory(szPathName,
#if 0
(LPSECURITY_ATTRIBUTES) NULL))
#else
&sa))
#endif
{
#if 0
wcscpy(lpPathName + sizeof("SAFER"), L"\\TMP");
#elif 0
wmemcpy(lpPathName + sizeof("SAFER"), L"\\TMP", sizeof("\\TMP"));
#else
lpPathName[sizeof("SAFER")] = L'\\';
#endif
PrintConsole(hConsole,
L"%lu\t%ls\n",
SRPLevel(hConsole), szPathName);
#if 0
wcscpy(lpPathName + sizeof("SAFER"), L".TMP");
#elif 0
wmemcpy(lpPathName + sizeof("SAFER"), L".TMP", sizeof(".TMP"));
#else
lpPathName[sizeof("SAFER")] = L'.';
#endif
if (!RemoveDirectory(szPathName))
PrintConsole(hConsole,
L"RemoveDirectory() returned error %lu for directory \'%ls\'\n",
GetLastError(), szPathName);
}
else
{
dwError = GetLastError();
if (dwError != ERROR_ACCESS_DENIED)
PrintConsole(hConsole,
L"CreateDirectory() returned error %lu for directory \'%ls\'\n",
dwError, szPathName);
else
dwError = ERROR_SUCCESS;
}
}
#if 0
wcscpy(lpPathName, L"\\*");
#elif 0
wmemcpy(lpPathName, L"\\*", sizeof("\\*"));
#else
// lpPathName[0] = L'\\';
lpPathName[1] = L'*';
lpPathName[2] = L'\0';
#endif
hFindFile = FindFirstFile(szPathName, &wfd);
if (hFindFile != INVALID_HANDLE_VALUE)
{
do
{
if (((wfd.dwFileAttributes & FILE_ATTRIBUTE_DIRECTORY) != FILE_ATTRIBUTE_DIRECTORY)
|| ((wfd.dwFileAttributes & FILE_ATTRIBUTE_REPARSE_POINT) == FILE_ATTRIBUTE_REPARSE_POINT))
continue;
#if 0
if ((wcscmp(wfd.cFileName, L".") == 0)
|| (wcscmp(wfd.cFileName, L"..") == 0))
continue;
#elif 0
if ((wmemcmp(wfd.cFileName, L".", sizeof(".")) == 0)
|| (wmemcmp(wfd.cFileName, L"..", sizeof("..")) == 0))
continue;
#else
if ((wfd.cFileName[0] == L'.')
&& (wfd.cFileName[1] == L'\0'))
continue;
if ((wfd.cFileName[0] == L'.')
&& (wfd.cFileName[1] == L'.')
&& (wfd.cFileName[2] == L'\0'))
continue;
#endif
dwFileName = wcslen(wfd.cFileName);
#if 0
wcscpy(lpPathName + 1, wfd.cFileName);
#else
wmemcpy(lpPathName + 1, wfd.cFileName, dwFileName);
#endif
dwError = Traverse(hConsole, dwPathName + 1 + dwFileName);
}
while (FindNextFile(hFindFile, &wfd));
#if 0
wcscpy(lpPathName, L"\\*");
#elif 0
wmemcpy(lpPathName, L"\\*", sizeof("\\*"));
#else
lpPathName[1] = L'*';
lpPathName[2] = L'\0';
#endif
dwError = GetLastError();
if (dwError != ERROR_NO_MORE_FILES)
PrintConsole(hConsole,
L"FindNextFile() returned error %lu for path \'%ls\'\n",
dwError, szPathName);
else
dwError = ERROR_SUCCESS;
if (!FindClose(hFindFile))
PrintConsole(hConsole,
L"FindClose() returned error %lu for path \'%ls\'\n",
GetLastError(), szPathName);
}
else
{
dwError = GetLastError();
if (dwError != ERROR_FILE_NOT_FOUND)
PrintConsole(hConsole,
L"FindFirstFile() returned error %lu for path \'%ls\'\n",
dwError, szPathName);
else
dwError = ERROR_SUCCESS;
}
// lpPathName[0] = L'\0';
return dwError;
}
__declspec(noreturn)
VOID CDECL wmainCRTStartup(VOID)
{
#ifndef _WIN64
BOOL bWoW64;
LPVOID lpWoW64;
#endif
DWORD dwPathName;
DWORD dwError;
HANDLE hConsole = GetStdHandle(STD_ERROR_HANDLE);
if (hConsole == INVALID_HANDLE_VALUE)
dwError = GetLastError();
else
{
dwPathName = GetSystemWindowsDirectory(szPathName, sizeof(szPathName) / sizeof(*szPathName));
if (dwPathName == 0)
PrintConsole(hConsole,
L"GetSystemWindowsDirectory() returned error %lu\n",
dwError = GetLastError());
else
#ifdef _WIN64
dwError = Traverse(hConsole, dwPathName);
#else
if (!IsWow64Process(GetCurrentProcess(), &bWoW64))
PrintConsole(hConsole,
L"IsWow64Process() returned error %lu\n",
dwError = GetLastError());
else
if (!bWoW64)
dwError = Traverse(hConsole, dwPathName);
else
if (!Wow64DisableWow64FsRedirection(&lpWoW64))
PrintConsole(hConsole,
L"Wow64DisableWow64FsRedirection() returned error %lu\n",
dwError = GetLastError());
else
{
dwError = Traverse(hConsole, dwPathName);
if (!Wow64RevertWow64FsRedirection(lpWoW64))
PrintConsole(hConsole,
L"Wow64RevertWow64FsRedirection() returned error %lu\n",
GetLastError());
}
#endif
}
ExitProcess(dwError);
}
-
Build the console application SAFER.COM from the
source file SAFER.C created in the previous step:
SET CL=/GAFy /Oxy /W4 /Zl
SET LINK=/DEFAULTLIB:ADVAPI32.LIB /DEFAULTLIB:KERNEL32.LIB /DEFAULTLIB:USER32.LIB /ENTRY:wmainCRTStartup /LARGEADDRESSAWARE /NOCOFFGRPINFO /OSVERSION:5.1 /SUBSYSTEM:CONSOLE /SWAPRUN:CD,NET /VERSION:0.815
CL.EXE /FeSAFER.COM SAFER.C
The console application SAFER.COM enumerates all
(sub)directories underneath the Windows directory
%SystemRoot%\, attempts to create an
Alternate Data Stream SAFER.TMP on each of
them, then either a file or a subdirectory SAFER.TMP in
each of them, queries the SAFER level for every file
written or directory created and prints it followed by the pathname.
For details and reference see the
MSDN articles
Compiler Options
and
Linker Options.
Note: if necessary, see the
MSDN article
Use the Microsoft C++ toolset from the command line
for an introduction.
Note: SAFER.COM is a pure
Win32 console application and builds without the
MSVCRT
libraries.
Microsoft (R) 32-bit C/C++ Optimizing Compiler Version 16.00.40219.01 for 80x86
Copyright (C) Microsoft Corporation. All rights reserved.
SAFER.C
SAFER.C(62) : warning C4090: 'function' : different 'const' qualifiers
SAFER.C(110) : warning C4090: 'initializing' : different 'const' qualifiers
SAFER.C(113) : warning C4090: 'initializing' : different 'const' qualifiers
SAFER.C(202) : warning C4090: 'function' : different 'const' qualifiers
SAFER.C(259) : warning C4090: 'function' : different 'const' qualifiers
Microsoft (R) Incremental Linker Version 10.00.40219.386
Copyright (C) Microsoft Corporation. All rights reserved.
…
-
Create the text file SAFER.XML with the following
content in the directory where you built the console application
SAFER.COM:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<!-- Copyright (C) 2004-2024, Stefan Kanthak -->
<assembly manifestVersion="1.0" xmlns="urn:schemas-microsoft-com:asm.v1">
<assemblyIdentity name="eSKamation.Tools.SAFER Loophole Detector Command" processorArchitecture="*" type="win32" version="0.8.1.5" />
<application xmlns="urn:schemas-microsoft-com:asm.v3">
<windowsSettings>
<longPathAware xmlns="http://schemas.microsoft.com/SMI/2016/WindowsSettings">true</longPathAware>
</windowsSettings>
</application>
<compatibility xmlns="urn:schemas-microsoft-com:compatibility.v1">
<application>
<supportedOS Id="{e2011457-1546-43c5-a5fe-008deee3d3f0}" />
<supportedOS Id="{35138b9a-5d96-4fbd-8e2d-a2440225f93a}" />
<supportedOS Id="{4a2f28e3-53b9-4441-ba9c-d69d4a4a6e38}" />
<supportedOS Id="{1f676c76-80e1-4239-95bb-83d0f6d0da78}" />
<supportedOS Id="{8e0f7a12-bfb3-4fe8-b9a5-48fd50a15a9a}" />
</application>
</compatibility>
<description>SAFER Loophole Detector Command</description>
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2">
<security>
<requestedPrivileges>
<requestedExecutionLevel level="asInvoker" uiAccess="false" />
</requestedPrivileges>
</security>
</trustInfo>
</assembly>
Note: an
Application Manifest
is mandatory to disable the
filesystem virtualisation
for 32-bit processes and to enable
long
pathnames for the functions of the Win32
API!
New UAC Technologies for Windows Vista
-
Embed the application manifest
SAFER.XML created in
the previous step in the console application SAFER.COM:
MT.EXE /CANONICALIZE /MANIFEST SAFER.XML /OUTPUTRESOURCE:SAFER.COM
Mt.exe
Microsoft (R) Manifest Tool version 6.1.7716.0
Copyright (c) Microsoft Corporation 2009.
All rights reserved.
-
Finally execute the console application
SAFER.COM
built in the previous steps as unprivileged (standard) user to
detect all directories beneath the Windows directory
%SystemRoot%\ where users can write and (still)
execute:
.\SAFER.COM
Caveat: the console application
SAFER.COM can but detect user-writable directories only
in paths where access permissions allow to list their contents!
FindFirstFile() returned error 5 for path 'C:\Windows\appcompat\Programs\*'
FindFirstFile() returned error 5 for path 'C:\Windows\CSC\*'
FindFirstFile() returned error 5 for path 'C:\Windows\LiveKernelReports\*'
FindFirstFile() returned error 5 for path 'C:\Windows\Logs\SystemRestore\*'
FindFirstFile() returned error 5 for path 'C:\Windows\ModemLogs\*'
FindFirstFile() returned error 5 for path 'C:\Windows\PLA\Reports\*'
FindFirstFile() returned error 5 for path 'C:\Windows\PLA\Rules\*'
FindFirstFile() returned error 5 for path 'C:\Windows\PLA\Templates\*'
FindFirstFile() returned error 5 for path 'C:\Windows\Prefetch\*'
FindFirstFile() returned error 5 for path 'C:\Windows\Provisioning\Autopilot\*'
0 C:\Windows\Registration\CRMLog:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\Registration\CRMLog:SAFER.TMP'
0 C:\Windows\Registration\CRMLog\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\Resources\Themes\aero\VSCache\*'
FindFirstFile() returned error 5 for path 'C:\Windows\security\audit\*'
FindFirstFile() returned error 5 for path 'C:\Windows\security\cap\*'
FindFirstFile() returned error 5 for path 'C:\Windows\ServiceProfiles\LocalService\*'
FindFirstFile() returned error 5 for path 'C:\Windows\ServiceProfiles\NetworkService\*'
FindFirstFile() returned error 5 for path 'C:\Windows\ServiceState\*'
0 C:\Windows\System32\Com\dmp:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\System32\Com\dmp:SAFER.TMP'
0 C:\Windows\System32\Com\dmp\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\System32\Com\dmp\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\config\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\Configuration\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\drivers\DriverData\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\DriverState\*'
0 C:\Windows\System32\FxsTmp:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\System32\FxsTmp:SAFER.TMP'
0 C:\Windows\System32\FxsTmp\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\System32\ias\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\LogFiles\WMI\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\MsDtc\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\networklist\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\SleepStudy\*'
0 C:\Windows\System32\spool\drivers\color:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\System32\spool\drivers\color:SAFER.TMP'
0 C:\Windows\System32\spool\drivers\color\SAFER.TMP
0 C:\Windows\System32\spool\PRINTERS:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\System32\spool\PRINTERS:SAFER.TMP'
0 C:\Windows\System32\spool\PRINTERS\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\System32\spool\PRINTERS\*'
0 C:\Windows\System32\spool\SERVERS:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\System32\spool\SERVERS:SAFER.TMP'
0 C:\Windows\System32\spool\SERVERS\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\System32\spool\SERVERS\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\sru\*'
0 C:\Windows\System32\Tasks:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\System32\Tasks:SAFER.TMP'
0 C:\Windows\System32\Tasks\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\System32\Tasks\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\wbem\MOF\*'
FindFirstFile() returned error 5 for path 'C:\Windows\System32\WDI\*'
FindFirstFile() returned error 5 for path 'C:\Windows\SystemTemp\*'
0 C:\Windows\SysWOW64\Com\dmp:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\SysWOW64\Com\dmp:SAFER.TMP'
0 C:\Windows\SysWOW64\Com\dmp\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\SysWOW64\Com\dmp\*'
FindFirstFile() returned error 5 for path 'C:\Windows\SysWOW64\config\*'
FindFirstFile() returned error 5 for path 'C:\Windows\SysWOW64\Configuration\*'
0 C:\Windows\SysWOW64\FxsTmp:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\SysWOW64\FxsTmp:SAFER.TMP'
0 C:\Windows\SysWOW64\FxsTmp\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\SysWOW64\Msdtc\*'
FindFirstFile() returned error 5 for path 'C:\Windows\SysWOW64\networklist\*'
FindFirstFile() returned error 5 for path 'C:\Windows\SysWOW64\sru\*'
0 C:\Windows\SysWOW64\Tasks:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\SysWOW64\Tasks:SAFER.TMP'
0 C:\Windows\SysWOW64\Tasks\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\SysWOW64\Tasks\*'
0 C:\Windows\Tasks:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\Tasks:SAFER.TMP'
0 C:\Windows\Tasks\SAFER.TMP
0 C:\Windows\Temp:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\Temp:SAFER.TMP'
0 C:\Windows\Temp\SAFER.TMP
FindFirstFile() returned error 5 for path 'C:\Windows\Temp\*'
0 C:\Windows\tracing:SAFER.TMP
DeleteFile() returned error 5 for alternate data stream 'C:\Windows\tracing:SAFER.TMP'
0 C:\Windows\tracing\SAFER.TMP
Caveat: deletion of the
Alternate Data Stream SAFER.TMP from some
user-writable directories fails due to their access permissions!
Update
All setup scripts support an update from any previous version: just
install their current version!
Upgrade
The setup script
NTX_SAFER.INF
supports the upgrade from any version of
NT6_SAFER.INF:
just install its current version!
Deinstallation
Deinstallation requires administrative privileges and access rights.
On Windows XP and Windows Server 2003,
open the Add/Remove Programs applet of the
Control Panel,
tick the checkbox Updates
, select the entry
Softwarebeschränkungsrichtlinien für 'Windows XP/2003 [R2]'
underneath Systemkonfiguration
and click the
Remove button.
On Windows Vista and newer versions of
Windows NT, open the Control Panel and
click the entry View installed updates underneath the
Programs and Features or Programs
category.
In Installed Updates select the entry
Softwarebeschränkungsrichtlinien für 'Windows Vista/2008 [R2]/7'
underneath Systemkonfiguration
and click the
Uninstall
menu entry.
Note: deinstallation neither removes the file
%SystemRoot%\System32\GroupPolicy\Machine\Registry.pol
nor any SAFER settings and rules from it.
Bugs
ATTENTION: versions of NT6_SAFER.INF
and NT6_SUPER.INF prior to 2017-03-08 had a bug:
instead of adding the Registry entry which prevents
unprivileged users from logging on in Safe Mode
they removed
it!
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"SafeModeBlockNonAdmins"=dword:00000001 ; Disable 'Standard Users' in 'Safe Mode'
Note: since this Registry entry does
not exist in standard installations of
Windows™ NT
it is unlikely that this bug had a negative impact.
ATTENTION: versions of NTX_SAFER.INF
prior to 2022-07-29 had a bug on 64-bit installations: instead to
add the path rules
%SystemRoot%\System32\Microsoft\Crypto\RSA\MachineKeys,
%SystemRoot%\System32\Microsoft\Crypto\RSA\MachineKeys:*
and
%SystemRoot%\SysNative\Microsoft\Crypto\RSA\MachineKeys:*
it added the latter thrice!
Contact
If you miss anything here, have additions, comments, corrections,
criticism or questions, want to give feedback, hints or tipps,
report broken links, bugs, deficiencies, errors, inaccuracies,
misrepresentations, omissions, shortcomings, vulnerabilities or
weaknesses, …: don’t hesitate to
contact me
and feel free to ask, comment, criticise, flame, notify or report!
Use the
X.509
certificate
to send
S/MIME
encrypted mail.
Note: email in weird format and without a proper
sender name is likely to be discarded!
I dislike
HTML (and even
weirder formats too) in email, I prefer to receive plain text.
I also expect to see your full (real) name as sender, not your
nickname.
I abhor top posts and expect inline quotes in replies.
Terms and Conditions
By using this site, you signify your agreement to these terms and
conditions. If you do not agree to these terms and conditions, do
not use this site!
- The software and the documentation on this site are provided
as is
without any warranty, neither express nor implied.
In no event will the author be held liable for any damage(s) arising
from the use of the software or the documentation.
- Permission is granted to use the current version of
the software and the current version of the
documentation solely for personal private and non-commercial
purposes.
An individuals use of the software or the documentation in his or
her capacity or function as an agent, (independent) contractor,
employee, member or officer of a business, corporation or
organisation (commercial or non-commercial) does not qualify as
personal private and non-commercial purpose.
- Without written approval from the author the software or the
documentation must not be used for a business, for
commercial, corporate, governmental, military or organisational
purposes of any kind, or in a commercial, corporate, governmental,
military or organisational environment of any kind.
- Redistribution of the software and the documentation is allowed only
in unmodified form of its current version and free
of charge.
Data Protection Declaration
This web page records no (personal) data and stores no
cookies
in the web browser.
The web service is operated and provided by
Telekom Deutschland GmbH
Business Center
D-64306 Darmstadt
Germany
<hosting@telekom.de>
+49 800 5252033
The web service provider stores a session cookie
in the web
browser and records every visit of this web site with the following
data in an access log on their server(s):
- the (pseudonymised)
IP address;
- the date and time of the request;
- the URL of
the requested web page or file;
- the Referer and User-Agent
HTTP
headers sent by the web browser;
- the result (success or failure) of the request;
- the amount of data received and sent.
Copyright © 1995–2024 • Stefan Kanthak •
<stefan.kanthak@nexgo.de>
![Screen shot of antivirus software outsmarted by malware via SAFER rules [Screen shot of antivirus software outsmarted by malware via SAFER rules]](https://blog.trendmicro.com/trendlabs-security-intelligence/files/2014/06/blocked.png) On the right, the screen shot of a message box shows antivirus
software which is disabled by
malware (ab)using
Software Restriction Policies, i.e. this antivirus
software was even unable to protect itself!
On the right, the screen shot of a message box shows antivirus
software which is disabled by
malware (ab)using
Software Restriction Policies, i.e. this antivirus
software was even unable to protect itself!
![Screen shot of message from 'Command Processor' of Windows Vista for blocked program [Screen shot of message from 'Command Processor' of Windows Vista for blocked program]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure16(en-us,technet.10).jpg)
![Screen shot of message box from 'Windows Explorer' of Windows Vista for blocked program [Screen shot of message box from 'Windows Explorer' of Windows Vista for blocked program]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure15(en-us,technet.10).jpg)
![Screen shot of default 'User Account Control Settings' from Windows 7 [Screen shot of default 'User Account Control Settings' from Windows 7]](https://support.microsoft.com/library/images/2692682.png) Note: on Windows 7 and newer versions
of Windows NT, with its default setting
UAC performs
silent (automatic) elevation for programs that
Note: on Windows 7 and newer versions
of Windows NT, with its default setting
UAC performs
silent (automatic) elevation for programs that
![Screen shot of 'Designated File Types Properties' from Windows Vista [Screen shot of 'Designated File Types Properties' from Windows Vista]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure03(en-us,technet.10).jpg) Subject to Software Restriction Policies are files that
match the definition of
Subject to Software Restriction Policies are files that
match the definition of ![Screen shot of 'Local Security Policy' snap-in from Windows Vista [Screen shot of 'Local Security Policy' snap-in from Windows Vista]](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/images/cc507878.figure13(en-us,technet.10).jpg)